I have been preparing some servers for a bunch of testing with PerformancePoint Server (more to follow on this later) which required me to change our MOSS service accounts. Reading around the steps to update these credentials appeared pretty straight forward but as usual MOSS' idiosyncrasies were all to apparent. Here's what i did and how i managed to solve the issues that arose. Hope it helps someone else with the same challenge.
The accounts to be changed were as follows:
- old_moss_admin ----> new_moss_admin
- old_ssp_ap ---->new_ssp_ap
- old_ap1_process ---->new_ap1_process
I followed the following MS KB instructions: '
How to change service accounts and service account passwords in SharePoint Server 2007 and in Windows SharePoint Services 3.0'
1. MOSS Admin Account Update To update the account old_moss_admin to new_moss_admin:
- Update the password for the account that is used by the Central Administration application pool. To do this, follow these steps:
- On all servers in the server farm, open a command prompt, type the following line, and then press ENTER:
cd %commonprogramfiles%\Microsoft Shared\Web server extensions\12\Bin
- On the server that hosts the Central Administration Web site, type the following line at the command prompt, and then press ENTER:
stsadm -o updatefarmcredentials -userlogin DomainName\UserName -password NewPassword
- On all other servers in the server farm, type the following line at the command prompt, and then press ENTER:
stsadm -o updatefarmcredentials -userlogin DomainName\UserName -password NewPassword -local
- Restart Microsoft Internet Information Services (IIS) 6.0. To do this, type the following line at the command prompt, and then press ENTER:
iisreset /noforce
- Verify that the Administration Application Pool Credential Deployment job definition is no longer displayed on the Timer Job Definitions page of SharePoint 3.0 Central Administration. To do this, follow these steps:
- Open SharePoint 3.0 Central Administration, click Operations, and then click Timer job definitions under Global Configuration.
- Verify that the Administration Application Pool Credential Deployment job definition is no longer displayed in the list.
Error: My Central Administration is now no longer available with the error: 'Service Unavailable'
- I checked & retyped the password in CA web app pool.
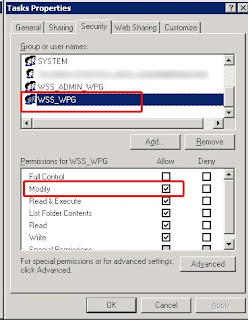
- I checked the WSS_WPG, WSS_RESTRICTED_WPG and WSS_ADMIN_WPG local groups on each of the servers - all seemed to be up to date.
- Restarting the CA web app pool makes no difference.
At this point i rolled back to the previous credentials. I then tried again from the start following the same steps above. Result - my Central Administration was still unavailable with the error: 'Service Unavailable'
- I checked the IIS_WPG local group on each server. The new_moss_admin account was not updated so i added it to the group.
I then discovered a couple of DCOM errors in the System Event viewer.
- I updated the new CA account 'new_moss_admin' to:
- IIS Admin Service
- IIS WAMREG Admin Service
- Restarted IIS.
Success: Central Admin is up and running again.
2. SSP Account Update To update the SSP account old_ssp_ap to new_ssp_ap:
Attempt 1 - The wrong way... - Open Central Administration
- Navigate to the Operations page
- Select Service Accounts
- Select the radio button Web app pool
- Select the web service - WSS Web App
- Select the App Pool - SSP1
- Select the radio button Configurable
- Input the new credentials
- Ok
- Restarted IIS on both my servers
Error: This had no effect other than stopping me from accessing the SSP. Checking in IIS the account was not updated to the new credentials. I then tried to update the accout via IIS but this had noeffect either and on opening the App Pool properties again i discovered that the account credentials had changed themselves back to the old account.
Attempt 2 - The right way... I then tried a different approach:
- Open Central Administration
- Navigate to the Shared Services Aministration homepage
- Hover over SSP1's title and select Edit Properties from the drop down.
- Scroll down to SSP Server Credentials
- Delete the old credentials and input the new account username & password
- Ok
- I then changed the SSP to be the default SSP.
- Open Compnent Services and update the DCOM services IIS Admin & IIS WAMREG with the new account.
- Restarted IIS on both my servers.
Checking IIS the account was still not updated to the new credentials and i still could not access the SSP website.
Success: 10 minutes later having searched on Google again and felt thoroughly annoyed at there being no pages I hadn't yet read on this topic I checked the SSP website again and it worked! Checking IIS the accounts have now updated to the new credentials.
At this stage I discovered some new errors in the Event View
- Application Server Administration job failed for service instance Microsoft.Office.Server.Search.Administration.SearchServiceInstance (5d77cabf-3414-40cc-a5ef-f30226a9288b).
Reason: The program attempted to update an object that was updated by another user.
- Eventid 6482 - Reason: Access to the path 'C:\WINDOWS\system32\drivers\etc\HOSTS' is denied.
This error was now occuring every minute.
The solution to this (and the previous error) can be found in my previous post here: http://bytelab.blogspot.com/2008/02/sharepoint-search-service-cannot-find.html
3. Application Pool Process Accout Update To update the web app pool process account old_ap1_process to new_ap1_process:
- Open Central Administration
- Navigate to the Operations page
- Select Service Accounts
- Select the radio button Web app pool
- Select the web service - WSS Web App
- Select the App Pool - MOSS Portal
- Select the radio button Configurable
- Input the new credentials
- Ok
- Open Compnent Services and update the DCOM services IIS Admin & IIS WAMREG with the new account.
- Restarted IIS on both my servers
Success: All updated and working ok.
************************************************************
Useful web sites i visited for this: